Two Iranian Hackers charged with $6 Million in SamSam Ransomware Attacks
Today the Department of Justice announced an indictment against two Iranian men: Faramarz Shahi Savandi and Mohammad Mehdi Shah Mansouri for their roles in stealing more than $6 Million in Ransom payments from a 34 month long ransomware campaign known as SamSam.
They were charged with:
18 U.S.C. § 371 - Conspiracy to Defraud the United States
18 U.S.C. § 1030(a)(5)(A) - knowingly causes the transmission of a program, information, code, or command, and as a result of such conduct, intentionally causes damage without authorization, to a protected computer;
18 U.S.C. § 1030(a)(7)(C) - demand or request for money or other thing of value in relation to damage to a protected computer, where such damage was caused to facilitate the extortion
18 U.S.C. § 1349 - Conspiracy
Victims were found in nearly every state:
Piecing together the case involved gaining cooperation from two European VPN services, and apparently at least one search engine. The indictment refers, for example, to the defendants using Bitcoin to pay for access to a European VPS, and then searching on May 15, 2016, for "kansasheart.com". The same day, they accessed the public website of Kansas Heart Hospital, and on May 18th, encrypted many key computers on the network and sent their ransom note.
Another key part of the investigation was gaining the cooperation of a Bitcoin Exchanger, which was able to demonstrate that on July 21, 2016, the defendants cashed out at least some of their ransomed Bitcoin into Iranian Rials and deposited it into bank accounts controlled by MANSOURI and SAVANDI.
Chat logs were also available to the investigators, as the indictment mentions contents of chat consistently throughout their timeline. Using the combination of events, some of the key dates were:
They were charged with:
18 U.S.C. § 371 - Conspiracy to Defraud the United States
18 U.S.C. § 1030(a)(5)(A) - knowingly causes the transmission of a program, information, code, or command, and as a result of such conduct, intentionally causes damage without authorization, to a protected computer;
18 U.S.C. § 1030(a)(7)(C) - demand or request for money or other thing of value in relation to damage to a protected computer, where such damage was caused to facilitate the extortion
18 U.S.C. § 1349 - Conspiracy
Victims were found in nearly every state:
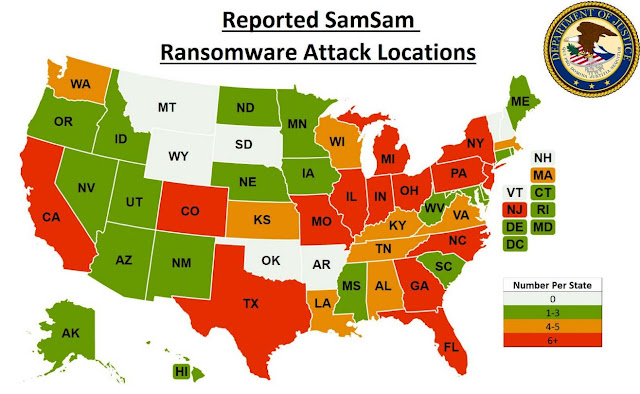 |
| Victim Locations from: https://www.justice.gov/opa/press-release/file/1114736/download |
Piecing together the case involved gaining cooperation from two European VPN services, and apparently at least one search engine. The indictment refers, for example, to the defendants using Bitcoin to pay for access to a European VPS, and then searching on May 15, 2016, for "kansasheart.com". The same day, they accessed the public website of Kansas Heart Hospital, and on May 18th, encrypted many key computers on the network and sent their ransom note.
Another key part of the investigation was gaining the cooperation of a Bitcoin Exchanger, which was able to demonstrate that on July 21, 2016, the defendants cashed out at least some of their ransomed Bitcoin into Iranian Rials and deposited it into bank accounts controlled by MANSOURI and SAVANDI.
Chat logs were also available to the investigators, as the indictment mentions contents of chat consistently throughout their timeline. Using the combination of events, some of the key dates were:
- December 14, 2015 - Defendants chatting about the development and functionality of SamSam.
- Jan 11, 2016 - Attack on Mercer County Business in New Jersey
- Feb 5, 2016 - Attack on Hollywood Presbyterian Medical Center
- March 27, 2016 - Attack on MedStar Health
- May 15, 2016 - Attack on Kansas Heart Hospital
- May 27, 2016 - Attack on University of Calgary
- July 27, 2016 - Attack on Nebraska Orthopedic Hospital
- April 25, 2017 - Attack on City of Newark, New Jersey
- January 18, 2018 - Attack on Allscripts Healthcare Solutions, Inc.
- February 19, 2018 - Attack on Colorado Department of Transportation
- March 22, 2018 - Attack on City of Atlanta, Georgia
- July 14, 2018 - Attack on LabCorp
- September 25, 2018 - Attack on the Port of San Diego
 |
| FBI Wanted Poster from: https://www.justice.gov/opa/press-release/file/1114746/download |

Comments
Post a Comment